The theft of portions of the source code is the second cybersecurity incident LastPass suffered in nine months. The company has confirmed the breach.
Sumeet Wadhwani Asst. Editor, Spiceworks Ziff Davis Last Updated: August 30, 2022
Password management services provider LastPass suffered the theft of proprietary information after a hacker used a compromised developer account to access the company’s development environment. The incident compromised portions of the company’s source code and some proprietary technical information.
LastPass explained that the incident occurred a couple of weeks ago when the unknown hacker gained access to its systems through a breached developer account, alerting the password management company of unusual activity.
While customer data and passwords remain unaffected despite the break-in, LastPass said the hacker could steal the source code and other proprietary data, given the compromised account had access to the LastPass development environment.
The company said, “We have determined that an unauthorized party gained access to portions of the LastPass development environment through a single compromised developer account and took portions of source code and some proprietary LastPass technical information.”
Avishai Avivi, CISO at SafeBreach, explained to Spiceworks how the theft of the source code could be damaging in the future. He said, “Bad actors will want source code for the same reason bank robbers will want floor plans to a bank. Being able to understand how the particular software works can potentially help the malicious actor identify its weak points and ways of gaining entry.”
“This doesn’t, however, mean that access to the bank’s floor plan, or even being able to compromise one of the bank employees, necessarily means that any money will be stolen.”
LastPass’ encrypted vaults store customer passwords that can be decrypted only using the master password. The master passwords weren’t compromised, considering LastPass doesn’t store them and are accessed through the Zero Knowledge security model described in the image below:
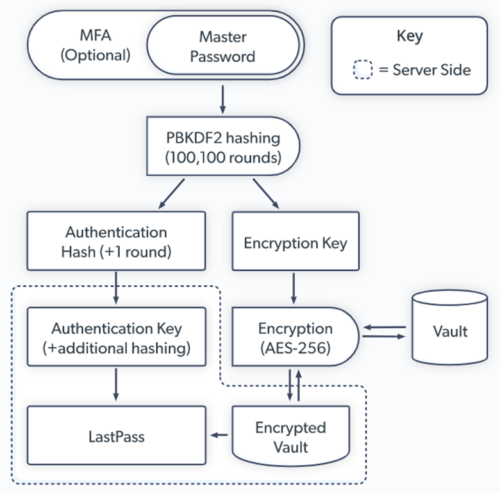
LastPass Zero Knowledge Security Model | Source: LastPass
“Zero knowledge means that no one has access to your master password or the data stored in your vault, except you. Not even LastPass,” the company notes on its website. Late in 2021, LastPass was suggestively victimized in a credential stuffing attack, the kind PBKDF2 hashing from the flowchart above is used to thwart.
