Press Release | May 24, 2023
The National Security Agency (NSA) and partners have identified indicators of compromise (IOCs) associated with a People’s Republic of China (PRC) state-sponsored cyber actor using living off the land techniques to target networks across U.S. critical infrastructure.
“Cyber actors find it easier and more effective to use capabilities already built into critical infrastructure environments. A PRC state-sponsored actor is living off the land, using built-in network tools to evade our defenses and leaving no trace behind,” said Rob Joyce, NSA Cybersecurity Director. “That makes it imperative for us to work together to find and remove the actor from our critical networks.”
To assist network defenders to hunt and detect this type of PRC actor malicious activity on their systems, NSA is leading U.S. and Five Eyes partner agencies in publicly releasing the “People’s Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection” Cybersecurity Advisory (CSA) today. The partner agencies include:
• U.S. Cybersecurity and Infrastructure Security Agency (CISA)
• U.S. Federal Bureau of Investigation (FBI)
• Australian Cyber Security Centre (ACSC)
• Canadian Centre for Cyber Security (CCCS)
• New Zealand National Cyber Security Centre (NCSC-NZ)
• United Kingdom National Cyber Security Centre (NCSC-UK)
“For years, China has conducted operations worldwide to steal intellectual property and sensitive data from critical infrastructure organizations around the globe,” said Jen Easterly, CISA Director. “Today’s advisory, put out in conjunction with our US and international partners, reflects how China is using highly sophisticated means to target our nation’s critical infrastructure. This joint advisory will give network defenders more insights into how to detect and mitigate this malicious activity. At the same time, we must recognize the agility and capability of PRC cyber actors, and continue to focus on strong cybersecurity practices like network segmentation and ongoing investments in promoting the resilience of critical functions under all conditions. As our nation’s cyber defense agency, CISA stands ready to aid any organization affected and we encourage all organizations to visit our webpage for guidance and resources to make their networks more resilient.”
“The FBI continues to warn against China engaging in malicious activity with the intent to target critical infrastructure organizations and use identified techniques to mask their detection,” said Bryan Vorndran, the FBI’s Cyber Division Assistant Director. “We, along with our federal and international partners, will not allow the PRC to continue to use these unacceptable tactics. The FBI strives to share information with our private sector partners and the public to ensure they can better protect themselves from this targeted malicious activity.”
“It is vital that operators of critical national infrastructure take action to prevent attackers hiding on their systems, as described in this joint advisory with our international partners,” said Paul Chichester, NCSC Director of Operations. “We strongly encourage UK essential service providers to follow our guidance to help detect this malicious activity and prevent persistent compromise.”
“The Canadian Centre for Cyber Security joins its international partners in sharing this newly identified threat and accompanying mitigation measures with critical infrastructure sectors,” said Sami Khoury, Head of the Canadian Centre for Cyber Security. “The interconnected nature of our infrastructures and economies highlights the importance of working together with our allies to identify and share real-time threat information.”
The CSA provides an overview of hunting guidance and associated best practices. It includes examples of the actor’s commands and detection signatures. The authoring agencies also includes a summary of indicators of compromise (IOC) values, such as unique command-line strings, hashes, file paths, exploitation of CVE-2021-40539 and CVE-2021-27860 vulnerabilities, and file names commonly used by this actor.
As one of their primary tactics, techniques, and procedures (TTP) of living off the land, the PRC actor uses tools already installed or built into a target’s system. This allows the actor to evade detection by blending in with normal Windows systems and network activities, avoiding endpoint detection and response (EDR) products, and limiting the amount of activity that is captured in default logging configurations.
NSA recommends network defenders apply the detection and hunting guidance in the CSA, such as logging and monitoring of command line execution and WMI events, as well as ensuring log integrity by using a hardened centralized logging server, preferably on a segmented network.
Defenders should also monitor logs for Event ID 1102, which is generated when the audit log is cleared.
The behavioral indicators noted in the CSA can also be legitimate system administration commands that appear in benign activity. Defenders must evaluate matches to determine the significance, applying their knowledge of the system and baseline behavior.
A new report from the cybersecurity and IT asset management company Ivanti, in which it surveyed about 800 government office workers across the world, found that younger employees were more likely to use the same or similar passwords for multiple devices or accounts. They were also more likely to share passwords between personal and work accounts.
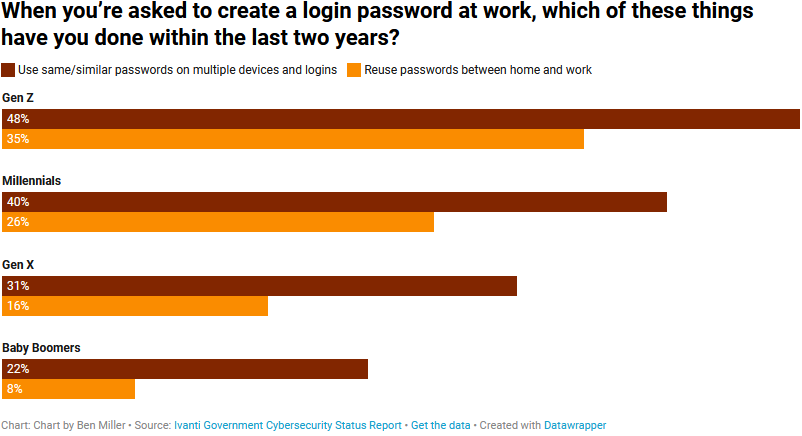
Other findings from the survey:
CyberheistNews Vol 13 #05 | January 31st, 2023
Cybersecurity Ventures released a new report that claims cybercrime is going to cost the world $8 trillion in 2023. If it were measured as a country, then cybercrime would be the world’s third largest economy after the U.S. and China.
The number sounds outlandish, but they stated: “We expect global cybercrime damage costs to grow by 15 percent per year over the next three years, reaching $10.5 trillion USD annually by 2025, up from $3 trillion USD in 2015.
“Cybercrime costs include damage and destruction of data, stolen money, lost productivity, theft of intellectual property, theft of personal and financial data, embezzlement, fraud, post-attack disruption to the normal course of business, forensic investigation, restoration and deletion of hacked data and systems, and reputational harm.”
The 2022 Official Cybercrime Report published by Cybersecurity Ventures and sponsored by eSentire, provides cyber economic facts, figures, predictions and statistics which convey the magnitude of the cyber threat we are up against, and market data to help understand what can be done about it.
Link to the article where you can download the report and see the VIDEO:
https://cybersecurityventures.com/cybercrime-to-cost-the-world-8-trillion-annually-in-2023/
Source: Paul Sigismondi, Ph.D., is a research physicist and educator. He has a B.S. in Physics from the University of California at Berkeley and a Ph.D. in Physics from the University of North Carolina at Chapel Hill. His research interests include theoretical astrophysics and quantum field theory.
Security from intruders is an ancient quandary and the internet has created new challenges. The purpose of this evaluation is to explore a digital identity and authentication solution called PhotolokÒ that addresses the security problem caused by the digital transformation that has invaded our daily lives. Since the digital world is still evolving, it’s helpful to begin with a review of security solutions because we still use century-old methods that will be replaced someday with digital solutions like Photolok.
A functional security system must allow quick, easy, and convenient entry to those with permission, but must make invasion by an unwanted intruder a highly unlikely occurrence. Ancient security arrangements typically involved gates, walls, watchtowers, moats, and armed personnel. In these arrangements, the main objective, which is still operative in modern systems, was to make invasion a taxing and dangerous enterprise for the intruder. Like today, robust and effective security required manpower and maintenance. Furthermore, the administrators had to acquire an awareness of the ever changing techniques that clever intruders were attempting in order to subvert the security systems in place.
The lock and key, which likely existed in rudimentary forms in ancient Egypt, provided localized security for people’s homes, safes, and the like. The advent of the combination lock eliminated the necessity of transporting keys and required merely recall of a numerical code to secure entry. Like the modern password system used for cybersecurity, these systems had their drawbacks.
From the standpoint of user convenience, what happens if the user loses his or her keys or forgets the combination? Spare sets of keys, pieces of paper with combinations written on them, keys placed under mats, and unlocked back doors and windows litter the praxis of those trying to prevent lockouts, while securing their property traditionally. They also create more possibilities for unwanted intruders to gain access to the keys or the combination. Since the user was not always able to access spare keys or a place where the combination is stored, the security system had to be penetrable without keys or the correct combination to be practicable. And, if a locksmith can pick a lock or crack a safe, then someone with nefarious intentions could certainly learn to do the same.
A combination lock has 59,280 distinct codes. There are less than 100,000 distinct lock and key combinations for a typical home door. If an 8-letter password is assigned at random to logon to an internet account, there are nearly 209 billion distinct possibilities for that password. In practice, a randomly assigned password is extremely difficult to remember. So instead, users are generally allowed to choose their own password
People tend to choose memorable passwords composed of common words and pass phrases. This significantly reduces the number of passwords practically in use. Zipf’s law, a well-known rule of thumb in statistics, states that the frequency of a given event within a distribution is inversely related to the rank of that event amongst the most highly ranked members of that distribution. Practically speaking, this means many people will choose the most common passwords in use. For example, in 2021, an estimated 2.5 million users adopted the most common password, “123456”, Nearly a million users chose “123456789”, and a little over 300,000 users chose “password”.
Zipf’s law has the effect of concentrating a population into the highly ranked events within that population. In fact, fitting the data for the top 7 passwords yields a frequency that is inversely proportional to the rank to 1.3 power. If this relationship were to hold consistently, then 50% of the passwords in use would be one of the top 7 most common passwords. This phenomenon gives internet intruders (bots and cyber hackers) a distinct advantage. (A ‘bot’ – short for robot – is a software program that performs automated, repetitive, pre-defined tasks. Bots typically imitate or replace human user behavior. Because they are automated, bots operate much faster than human users.)
Given that a modern intruder is often an automated bot that can make billions of attempts with the most common passwords on multiple targets each second, traditional passwords are vulnerable to statistical attack. Even, if a user is astute enough to choose a more secure password, there are other methods that bots can try in order to penetrate password secured systems, which include phishing, ransomware, malware, insider threats, and distributed denial of service attacks, to name a few.
reCAPTCHA is a common solution to prevent BOT attacks. After the user has successfully entered their username and password, they are prompted to prove they are a human either properly identifying distorted text or by identifying images with similar content. At this point, every hacker has seen the limited suite of images used in the reCAPTCHA algorithm and can use this information to their advantage. In addition, off the shelf software can now crack the reCAPTCHA algorithm 70% of the time.
The rapid advancement and efficacy of techniques currently employed by cyber hackers necessitate more robust security systems. Traditional password secured systems are also vulnerable to non-statistical attacks (phishing, ransomware, and man in the middle attacks, etc.) and to statistical attack, especially when sufficient latitude is given to the user in choosing a password. Photolok is a system that is nearly impervious to non-statistical attack and has an incredibly low probability of statistical attacks, comparable to truly randomly assigned passwords. At the same time, it is far more convenient to the user in terms of recall than a randomly assigned password that the user did not participate in choosing.
Photolok is a novel concept that employs proprietary-coded photos as the key to entry. The system can either assign the user photos or allow the user to choose photos from a proprietary library of photos that currently number over 6400. At login, the user is prompted for an email address. As an added security feature, there is an option that requires the user to input an access code that is emailed or texted to them after they have entered their email address. Subsequently, the user must locate one of their account photos, which appears randomly amid a panel of photos.
The Photolok identity and authentication system can be customized to allow the user to choose up to 5 photos as well as label special security photos for 1-Time Use and Duress. This identity and authentication system is highly secure and easy to use given that the photos are easily recalled and must be spotted by a human. More importantly, Photolok also protects against most external attacks, including keylogging, shoulder surfing, phishing, ransomware, and man-in-the-middle attacks while preventing horizontal penetrations.
This leaves a statistical attack as the only viable means of penetrating the Photolok system. However, this is highly unlikely. The number of possible combinations formed by choosing a minimum 3 photos from a library of 6400 is nearly 44 billion, which is about 5.5 times the total population of the world. The number of people fully employed in the US is about 132 million. If every one of those workers participated in choosing 3 photos out of 6400, the probability that there would be at least one duplicate set of photos in that large sample is 0.32%. Even if the entire world’s population were given this task, the likelihood of at least one duplicate set of photos occurring within the choices is still only 17%. Therefore, penetration of the Photolok system is nearly impossible.
Furthermore, the above analysis overestimates the probability of breakthrough. There is no limit to complexity of the Photolok system. Photos can be added to the library. Administrators can also ask the users to choose more photos. As stated above, the choice of 3 photos is a minimum. In many cases, users will want to use 4 photos with nearly 69 trillion photo combinations. With the ability to change a few operational variables, security can be further enhanced in a flexible manner with no extra burden to the user – e.g., increasing the size of the proprietary photo library.
As opposed to passwords, bots can’t identify the photos to target. The randomization of photo localizations effectively neutralizes any automated attack. Furthermore, the bots won’t be able to collect the digital data behind the photos, which may change each time a login attempt occurs. With almost 100% certainty, any attempt at penetration by automated bot will result in failure and automatically locks the user’s account.
In conclusion, Photolok represents a significant and promising evolution in digital security systems. It seamlessly eliminates many of the flaws inherent in the present security paradigm. Most importantly, it enhances online digital security, while simultaneously reducing the burden on the user, which is critical for mass adoption.
Note: to learn more about Netlok’s Photolok logon solution, click www.netlok.com.
KnowBe4 recommends that everyone use a password manager to create and use strong passwords as a part of their password policy:
https://info.knowbe4.com/wp-password-policy-should-be
LastPass, one of the world’s most popular password managers, recently had a bad data breach as revealed here:
https://blog.lastpass.com/2022/12/notice-of-recent-security-incident/
LastPass divulged that although user’s plaintext passwords were not accessed, what the hackers did get included the following information:
The hackers also got LastPass user’s encrypted passwords for each stored logon. The encryption protection is strong AS LONG AS the master password users used for LastPass was strong. If you’re interested in a more detailed discussion, go here:
https://www.linkedin.com/pulse/just-how-bad-recent-lastpass-compromise-roger-grimes
In summary, if your LastPass password was at least 12-characters long (the current LastPass default), contained some complexity, wasn’t an easy-to-guess password, and was not used on any other site or service, then you’re probably OK. If not, you need to immediately change all your passwords, both the LastPass master password and all the passwords you stored in LastPass.
Spear Phishing Bonanza
However, the plaintext information that was stolen (listed above) is incredibly useful to any hacker doing social engineering and phishing. It allows an attacker to specifically target (i.e., spear phish) a potential victim using information not known to the general public and other hackers.
For example, with a list of the web sites that someone logs onto, a phisher can craft specific phishing emails that pretend to be from that web site. It could include the user’s name, telephone number and mailing address. Each added detail adds to the veil of false legitimacy to a social engineering email. Each included detail increases the percentage of people who will become victims.
Knowing people’s phone numbers and what websites they belong to opens up an avenue for a fake tech support call. Mailing addresses can allow elaborate scams through postal mail. Here’s a brazen example of such a scam:
https://www.nasdaq.com/articles/inside-the-scam%3A-victims-of-ledger-hack-are-receiving-fake-hardware-wallets-2021-06-17
The sky is the limit on the types of spear phishing scams that can be created and delivered using the information that was stolen in the LastPass breach. Kudos to LastPass for making sure the most critical user information, the user’s passwords, were stored in an encrypted state.
But this breach, like all the others before it, are calling into question about what type of user information should or shouldn’t be considered “critical information” and always stored in an encrypted state. If the information can be used to identify or contact you, it should probably be encrypted by default.
LastPass users were relieved to learn that their stored passwords were not directly compromised, but what information was taken by the hackers is likely to have spear phishing repercussions for years to come.
Blog post with links:
https://blog.knowbe4.com/heads-up-lastpass-attack-could-supercharge-spear-phishing-attacks
CyberheistNews Vol 12 #52 | December 28th, 2022
To start off I’m repeating the tradition of my same New Year’s wish as a newsletter editor since 1996: “A world without war, crime and insanity, where honest people can flourish, prosper and reach greater heights”.
At the end of the year I spend a few days reading all the IT security pundit’s 2023 predictions and synthesize them with my own perspective. The Crystal Ball editorial is the shortest of the year and takes the longest to write, but it’s fun.
President Ronald Reagan once said, “The future doesn’t belong to the fainthearted; it belongs to the brave.” Sci-fi writer William Gibson added a few decades later: “The future is already here, it’s just unevenly distributed.” So, what will come next in our world of cybersecurity as we head into 2023?
The industry as a whole covered the following topics: This year will bring significant shifts to the world of cybersecurity. We could very well see a barrage of nation-state cyberattacks inspired by Ukraine’s hybrid hot- and cyberwar, an increase in MFA attacks, innovative strikes against drones and space vehicles, and skyrocketing social engineering attacking social media with deepfakes.
As the reach of hacktivism continues to expand, organizations are being compelled to look beyond endpoint solutions and invest in new “umbrella” platforms like XDR, Managed XDR and HDR that can help them manage increasing Infosec complexities. Furthermore, ransomware is expected to remain a major threat as malicious actors experiment with new, even more damaging forms. We must be especially vigilant when it comes to emerging technologies such as self-driving automobiles, humanoid robots or the Metaverse that highly likely will provide cyber criminals with new attack surfaces. It is sure to be an eventful 2023.
As usual, I’m donning my asbestos undies, so you can safely flame my poor behind after reading the new 2023 predictions. Good riddance of ‘annus horribilis’ 2022 which was the year of permacrisis.
In “The Big Lessons From History”, financial writer Morgan Housel sums it up succinctly: “Risk is what you don’t see,” and “The riskiest stuff is always what you don’t see coming.” All the more reason to keep your eyes peeled and send monthly simulated phishing tests to keep your users on their toes!